Our Cybersecurity Partners
-
Increase Security Today
Get Started → -
Our Internship Program
Join Today → -
New Book Campaign
Pre-Order →
We Manage Cybersecurity Solution Built For Business Owners
Did you know?
Over 50% of all cyber attacks are done on SMBs (helpnetsecurity.com)
70 to 83% of SMBs are not prepared for a cyberattack (forbes.com)
95% of cybersecurity breaches occur as a result of human error (searchlogistics.com)
On average, hackers attack 26,000 times a day or every three seconds (forbes.com)
60% of small businesses that are victims of a cyber attack go out of business within six months (cybersecurityventures.com)
SMB Common Threats
Phishing Attacks
Phishing victims may inadvertently expose security vulnerabilities that attackers can exploit to gain unauthorized entry into systems, confidential information, and cause harm.
Malware Attacks
Malware attacks on SMBs /SMEs can result in data theft,
file encryption for ransom, or system damage causing
significant downtime.
Ransomware
Ransomware encrypting SMBs/ SMEs data can lead to paying a ransom to regain access, causing financial loss and business disruption.
User & Data Security
Inadequate user authentication and excessive sharing of company data may hold the company liable for any breach-related damages.
Insider Threats
Employee or authorized user misuse of access privileges can lead to data exfiltration or damage within company systems and services.
Leaked Credentials
Stolen data exposed on the dark web contains leaked credentials that can pose a critical risk to employees and businesses if left unchecked.
Cynitra Information Systems LLC
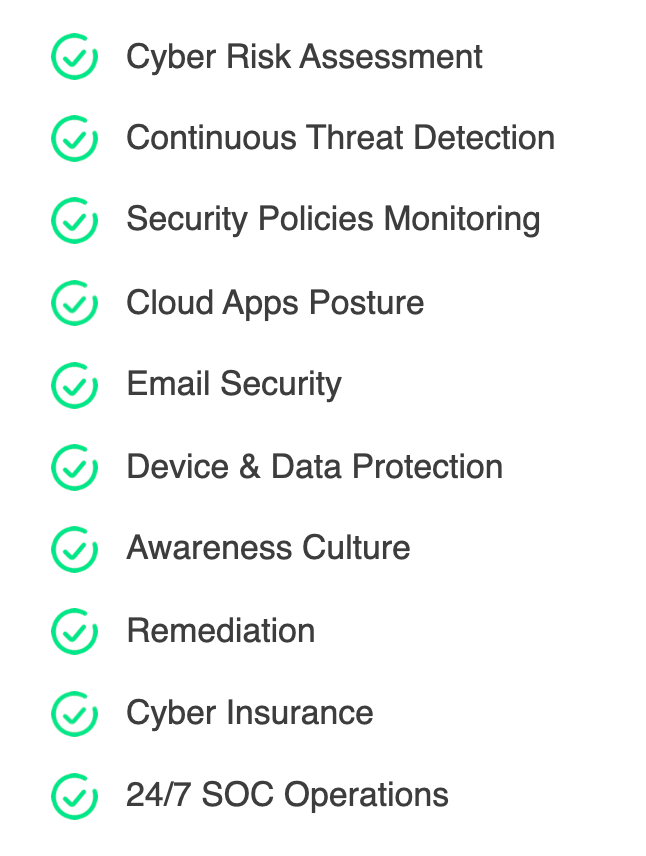
INTRODUCING GUARDZ
Guardz aims to create a safer digital world for all businesses, empowering MSPs and IT Pros to proactively secure and insure businesses holistically with a comprehensive suite of features across the most common attack vectors, including:

With Guardz, you can rest assured that your business will be protected from the outside in.
Note: Guardz is a platform that helps me with external cybersecurity risk assessments. I still have to go in and do internal cybersecurity risk assessments.
Protect Your Resources
Your Cyber Security Solutions
Phalanx helps with these common data security challenges:
● Reducing the risk of malicious actors gaining access to sensitive files and stealing information (e.g., ransomware, insider threat, data breach mitigation)
● Maintaining security on data stored on endpoints outside of network boundaries (e.g., mobile workstations/remote employees)
● Sharing information internally and externally (e.g., contractors) that's secure, traceable, and user-friendly
● Ensuring only the right people have access to the right information (i.e., Zero trust)
● Mitigating the risks of human error in data handling and transference (e.g. insider threat, specifically unwitting assets and negligence)
Our customer’s trust us to:
● Secure third-party file transfers & provide easy encrypted data access without relying on cloud storage
● Protect sensitive information (primarily costing, bidding, proposal information) & secure remote workers across multiple sites internationally
● Encrypt and trace CUI, PII, and export controlled information for components of CMMC and ITAR compliance
● Securely transfer CUI, PII, export controlled information, and wiring/payment information to third-parties
● Secure proprietary client information being stored in cloud and endpoint environments by a remote workforce
● Reduce the amount of unencrypted information residing on email servers
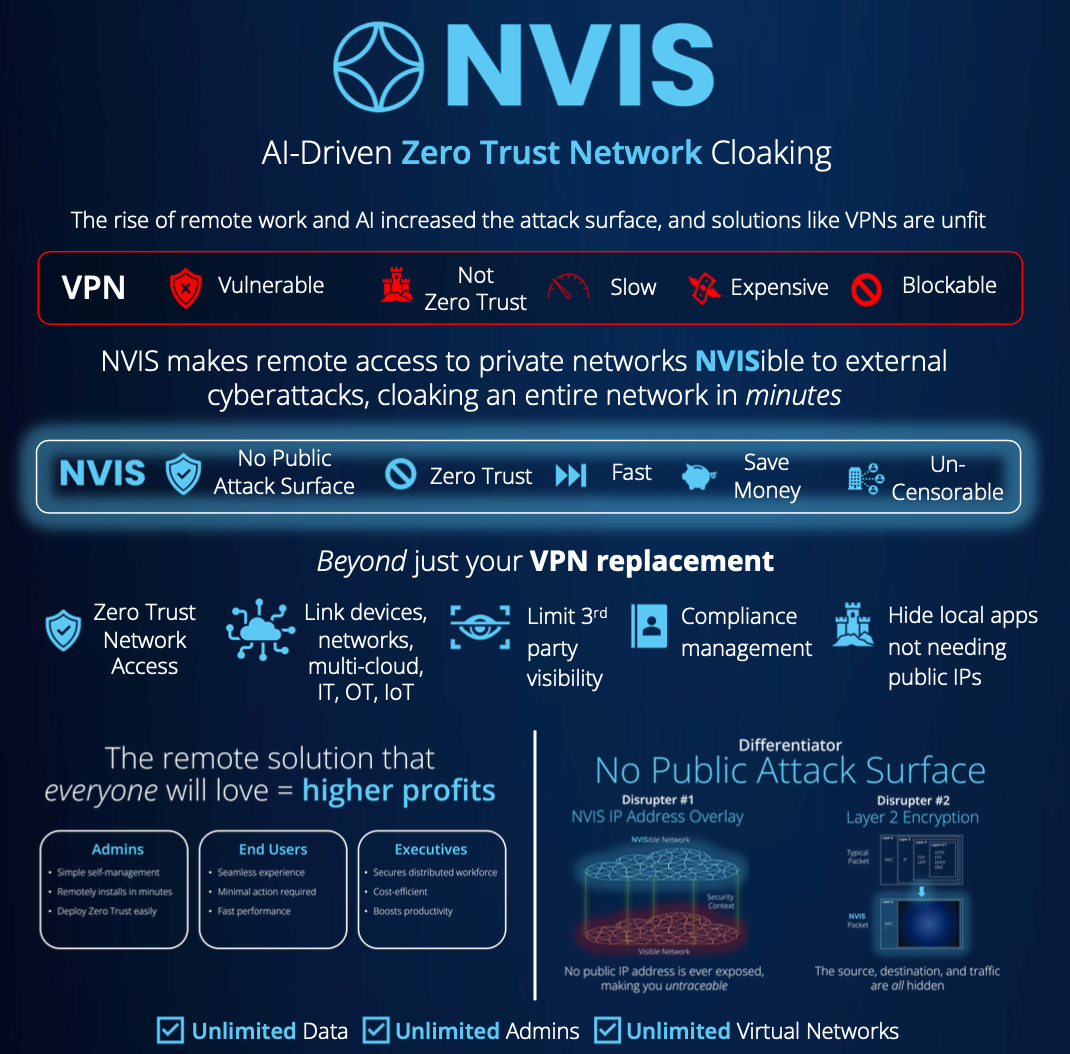
NVIS Overview: Illuminating the Essentials
Our Cybersecurity Partners
Vendor Information
Cage Code: 9KHX7
UEI: PNC4DZ53M265
FEIN: 83-2726917
DUNS: 117027160
222 N. Lafayette St. Suite 11, Shelby, NC 28150
All Rights Reserved | Cynitra Information Systems LLC